mirror of
https://github.com/UberGuidoZ/Flipper.git
synced 2024-12-22 14:30:21 +00:00
61 lines
3.1 KiB
Markdown
61 lines
3.1 KiB
Markdown
# Official info
|
|
|
|
The Wifi devboard ships with [Blackmagic firmware](https://github.com/flipperdevices/blackmagic-esp32-s2) installed. The Flipper documentation [is here](https://docs.flipperzero.one/development/hardware/wifi-debugger-module), and Blackmagic is [over here](https://black-magic.org/).
|
|
|
|
Quick start: Connect to the SSID `blackmagic` using the password `iamwitcher` or plug the wifi devboard in via USB.
|
|
|
|
# ESP32 Wi-Fi Pentest Tool
|
|
|
|
Check out [Frog's write-up](https://github.com/FroggMaster/ESP32-Wi-Fi-Penetration-Tool) and build for quick and easy flashing! Seriously, it's basically just a double-click.
|
|
|
|
# Some quick steps to get [Marauder](https://github.com/justcallmekoko/ESP32Marauder) installed<br>
|
|
(Direct from the dev WillStunForFood on Discord - check out [his video walkthrough](https://www.youtube.com/watch?v=_YLTpNo5xa0) too!):
|
|
|
|
- Plug the WiFi dev board directly into your PC
|
|
- Upload the MarauderOTA firmware from source via Arduino IDE
|
|
- Use the MarauderOTA firmware to flash the Marauder Flipper bin over WiFi
|
|
|
|
The first step in the wiki documentation [starts here](https://github.com/justcallmekoko/ESP32Marauder/wiki/flipper-zerowhile).<br>
|
|
(Then you should have the necessary links to the follow on documentation to get the firmware installed.)
|
|
|
|
ESP32-S2 is the correct board if you are installing on the Flipper WiFi Dev Board. <br>
|
|
If you are using the Marauder OTA method, you shouldn't have to install any libraries. <br>
|
|
The only other thing you should have to install is the boards for the ESP32 in the Arduino IDE and the drivers for the ESP32-S2.
|
|
|
|
Commands `channel`, `scanap`, `sniffbeacon`, `sniffdeauth`, `sniffpmkid`, `stopscan`, `clearap`
|
|
|
|
------------------------------------------------------------------------------
|
|
|
|
Example Attack Profile ([from Discord](https://discord.com/channels/740930220399525928/967843558520418384/997185157175988264)):
|
|
|
|
Use command `scanap` stop with `stopscan` when done.
|
|
|
|
List all found Beacons from previous steps via `list -a`
|
|
|
|
Note the enumeration of your target Beacon...
|
|
|
|
Use `select -a x` command to select your target. (x being your target # from previous step)
|
|
|
|
Execute chosen attack `attack -t deauth`
|
|
|
|
Use `stopscan` when done.
|
|
|
|
-----------------------------------------------------------------------------------
|
|
|
|
# Quick steps from Rabid Root...
|
|
|
|
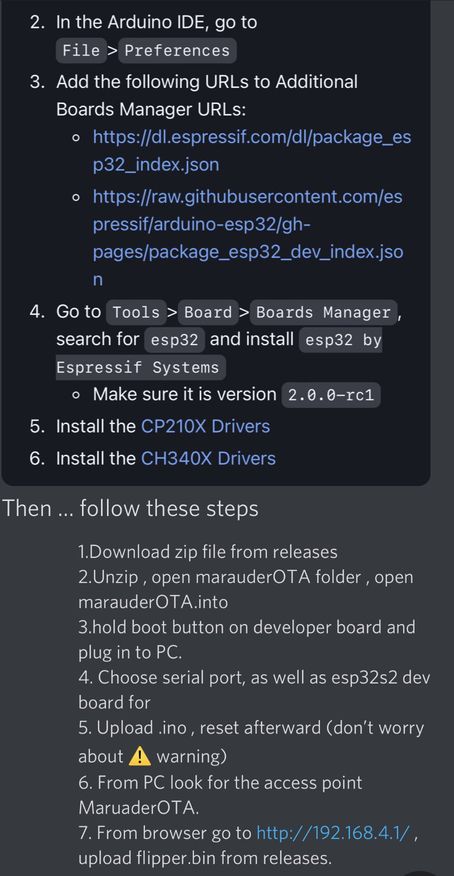<br>
|
|
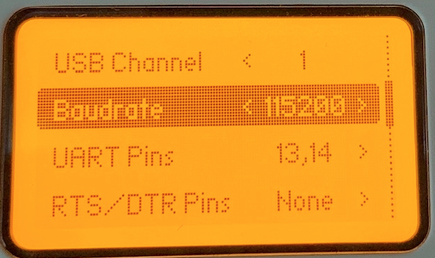
|
|
|
|
# AND a great step by step from E_Surge!
|
|
|
|
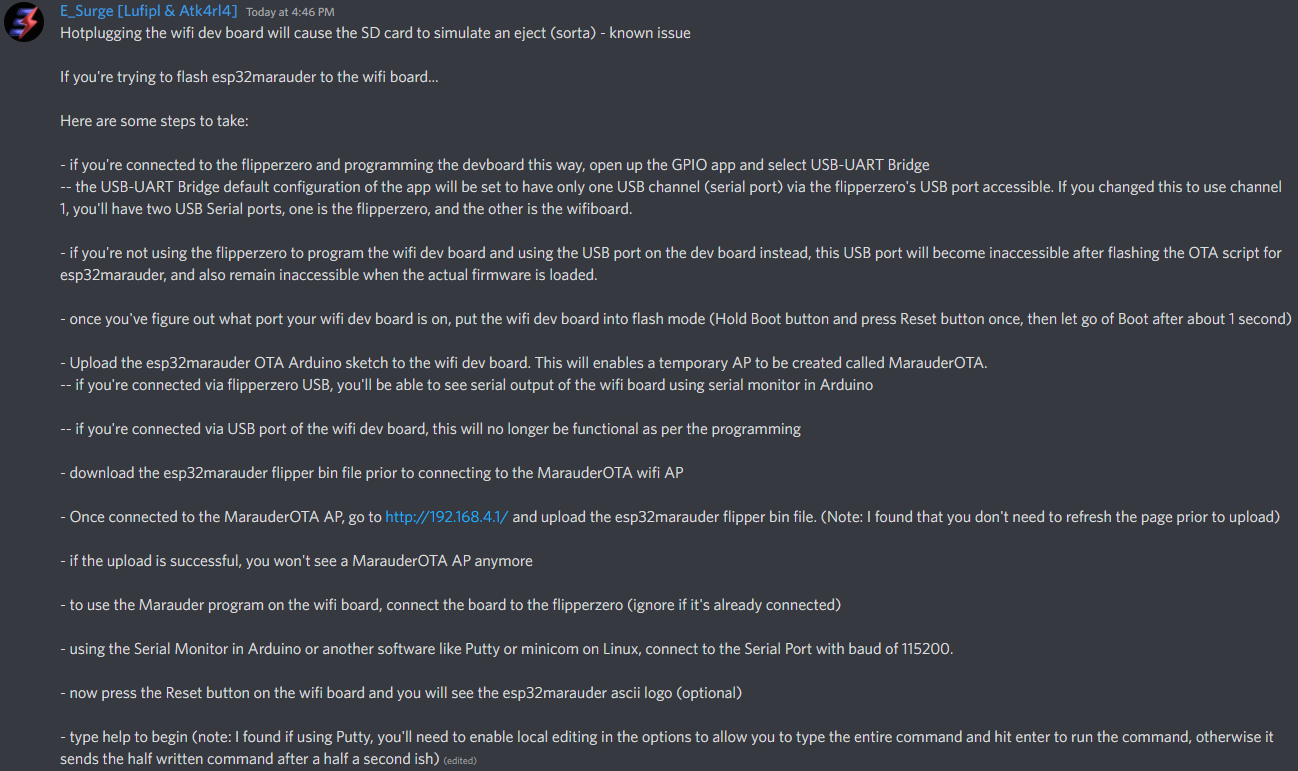
|
|
|
|
# If serial connection looks scrambled... (thanks Frog!)
|
|
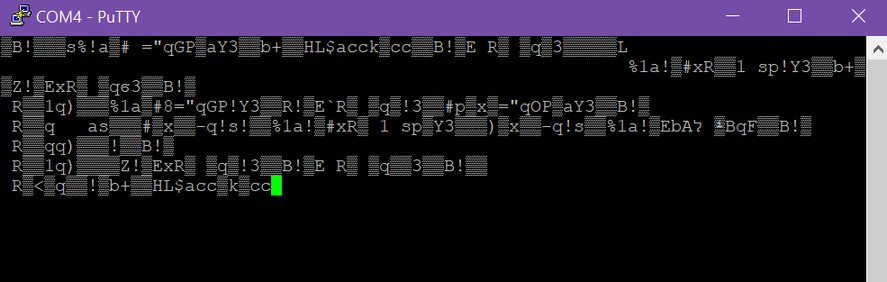
|
|
|
|
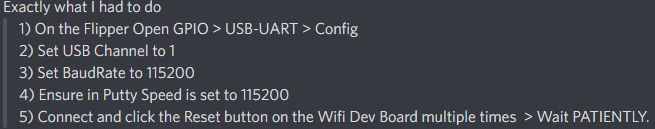
|
|
|
|
Frog also noted that it's wise to reflash the Flipper firmware if such issues are persisting.<br>
|
|
Start with the Official firmware, test, then move to a unlocked one if desired.
|